Understanding the Threat Landscape with MITRE ATT&CK and ClearQuery


In light of the multitude of recent events where everything seems to only entail a ransomware attack — it’s important to realize that a potential cyber adversary has many different motivations for attacking our IT infrastructure and many different techniques. It is also the case that there are numerous groups that are always on the lookout for opportunities to extract data, extort money, or deny services. Our abilities to quickly identify, ingest, and extract valuable intelligence from data is more important than ever given the fast-acting nature of these threats. The identification of techniques used allows us to create corporate policy to help mitigate these techniques and also ensure that our IT infrastructure remains free of malicious actors.
Finding Data
MITRE provides their knowledge base of adversary tactics and techniques and mechanisms to pull the data for the low price of free99. I utilized some of their pre-made scripts located on one of their github repos that provide an easy way to download the data used in this post in csv.
Utilizing these scripts I was able to pull the techniques, groups, software, and mitigations from the MITRE ATT&CK TAXII collection server and with a little denormalization was able to merge the data into a single CSV that would include all of this information linked to the various techniques and attackers that have been collected.
Ingesting Data
We’re going to be using ClearQuery to evaluate this data.
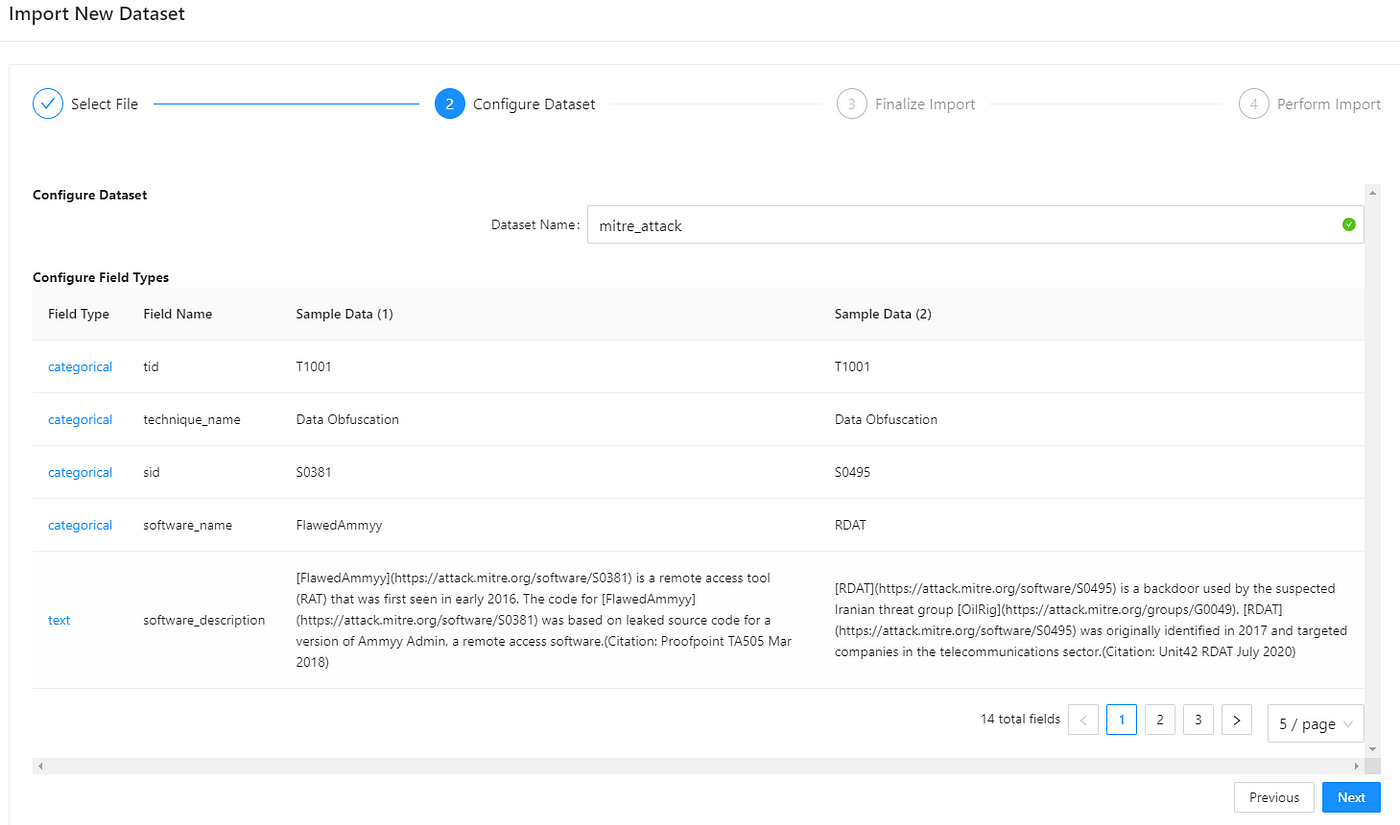
One of the great things about ClearQuery is how easy it makes it for non-technical users to be able to quickly ingest data through a common format such as CSV or Google Sheet and then it immediately provides some automated insights. Within 60 seconds of uploading your data to the system, you’re provided with a dashboard of insights that allow you to click, navigate, and filter through your data.
Threat Landscape
Once we’ve loaded the data, we’re able to begin looking through it in order to get an idea of what’s going on with the various attacking groups, techniques, and malicious software used within our dataset. ClearQuery’s automated insights provides an immediate break down of the top techniques, groups, and software within the dataset as well as some natural language statistics on the data as seen below.

Immediately we discover that within the data the top 5 threat groups are APT32, APT29, Lazarus Group, and APT28. We are also provided a snippet of statistical information telling us how much larger a threat APT32 is than the next top group of APT29.


We’re also provided with additional breakdowns of the Techniques, and Software that is most prevalent in the ATT&CK data that has been collected.
While understanding the techniques and groups involved in the threat landscape of cybersecurity it may be nice to see what techniques are shared amongst the Top 5 groups. To do this we perform a relationship discovery that will yield a graph of the interconnected groups and techniques.

We create a relationship discovery query of the group name with the technique names, and then filter based off the values of [APT32, APT29, Lazarus Group, APT28, Turla]. This will yield us a graph where the group name values must match.
After running that query, we’re provided a graph of interconnected group names, and techniques.
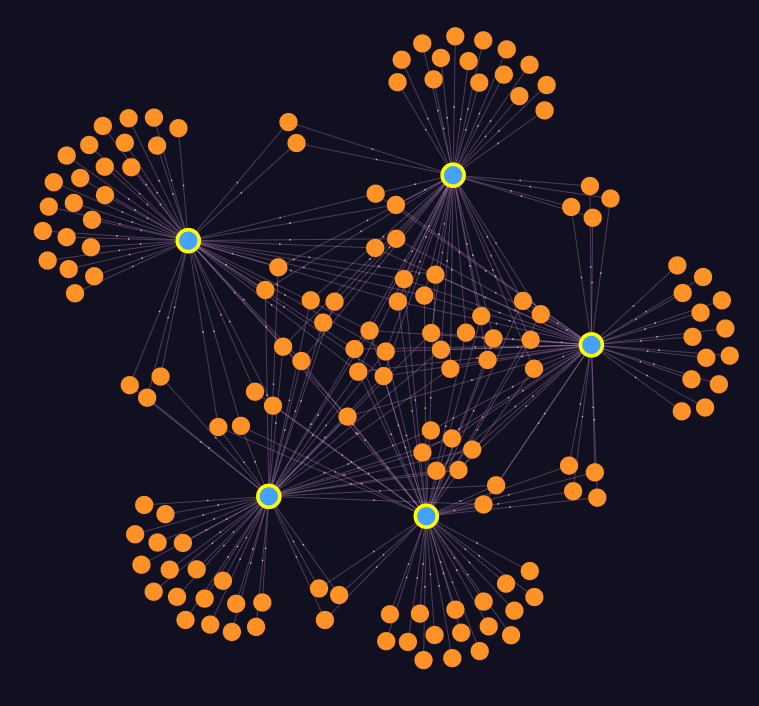

At-a-Glance we’re quickly provided with a relationship graph that provides an interesting matrix of techniques that are commonly shared between the threat groups as well as techniques that are not shared. Diving into the table of information, we can see the top techniques shared between groups within our ATT&CK data. Moussing over each blue point provides the group name, and the orange points are techniques used.
From any of these nodes, we’re able to complete a search of the automated insights to see how each technique or each group associated relates to other techniques, software, or mitigations involved.
Conclusions
Oftentimes we have to rely on a team of domain experts and data engineers to gain an appreciation and an understanding of the threat landscape facing our cyber infrastructures. With cyber-related datasets becoming more prevalent and being shared across more groups the ability to quickly tease out information in a short time-frame is important if we’re going to stay ahead of the advanced threats that are out there.
With ClearQuery we provide the ability to quickly triage, understand, and act on data by non-technical domain experts to help inform decision-makers with intelligence. Simply looking at the provided relationships table, we’re able to understand that many threats rely on spearphishing, malicious domains, malware, or malicious web services to attack your infrastructure. This information may lead companies to invest more heavily in the people aspect of their company to identify and react appropriately to these types of techniques in order to better protect their assets.
Please reach out if you have any questions or would like more information.
